In today’s fast-paced digital landscape, cloud environments have become the backbone of modern businesses. However, as organizations migrate their critical operations to the cloud, they face an ever-evolving threat landscape. Sophisticated cyberattacks, misconfigurations, and insider threats are just a few of the challenges cloud infrastructures must contend with daily. Traditional security tools often fall short in providing the visibility and agility needed to counter these threats effectively. This is where Cloud Detection and Response (CDR) steps in—offering a proactive, real-time solution designed to secure cloud environments, detect emerging threats, and respond swiftly to minimize damage. CDR is the modern shield businesses need to stay resilient in the face of these challenges.
What is Cloud Detection and Response (CDR)?
Cloud detection and response (CDR), also referred to as cloud-native detection and response (CNDR) and cloud threat detection and response (CTDR), provides threat prevention, detection, and response capabilities tailored for multicloud environments. It employs agentless technology to offer protection, real-time visibility, and identification of threats, vulnerabilities, misconfigurations, and compliance gaps without interfering with operations.
Why is CDR Essential for Organizations?
- The rise in cloud-based threats.
- Limitations of traditional detection and response systems.
- The need for real-time, automated responses in dynamic cloud environments.
The CDR Schema
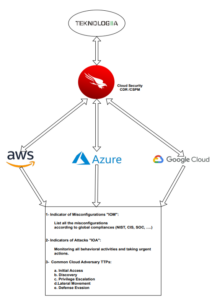
Key Features of an Effective CDR Solution
- Real-time threat detection
- Automated incident response
- Seamless integration with existing tools
- Advanced analytics and threat intelligence
- Compliance management
Benefits of Implementing CDR
- Visibility across cloud environments.
- Response time to mitigate threats.
- Protection of sensitive data.
- Business continuity by minimizing downtime.
Is your cloud security ready for modern threats?
How is your organization tackling cloud security? Contact Teknologiia for more details
Related Articles: Adopt a Cloud Protect your business from Cyberattacks
Stay Connected! Subscribe to our LinkedIn LinkedIn Newsletter for expert insights, compliance tips, and the latest security updates.



