Enhance Your Security Posture with CrowdStrike!
Maintaining compliance with regulatory standards is crucial for safeguarding your organization’s assets. By utilizing Center for Internet Security (CIS) Benchmarks and Defense Information Systems Agency (DISA) STIGs, you can proactively detect misconfigurations, fortify your environment against cyber threats, and ensure adherence to security requirements.
Configuration Assessment Overview
Assess assets in your environment for compliance with Falcon’s configuration assessment tools. Comply with regulatory reporting standards by using Center for Internet Security (CIS) benchmarks and Defense Information Systems Agency (DISA) Security Technical Information Guides (STIGs) to check your assets for misconfigurations. With this information, you can harden your Windows environments against common attack techniques, meet compliance and security requirements, and prepare for audits.
CIS benchmarks and DISA STIGs provide explicit guidance and qualifications for weak or misconfigured systems, including how to assess them. With configuration assessment, you can customize these standards to meet the specific compliance requirements of your environment.
Understanding Configuration Assessment
Configuration assessment gives you a real-time view into your security landscape so you can demonstrate compliance and ensure you’ve hardened your environment against security risks. Use Falcon’s configuration assessment tools alongside Falcon’s vulnerability management tools for a full picture of your assets and vulnerabilities, so you can address security concerns as soon as they arrive and keep your environment up-to-date with CIS recommendations. Configuration assessment only works on hosts that can run a Falcon sensor.
Your organization may need to view proactive security and compliance through a different lens than CIS benchmarks, so Falcon lists all the authorities who compliance requirements are met in addition to CIS:
- HIPAA
- ISO 27001
- NIST
- PCI
- SOC2
- SOX
Supported operating systems:
- Windows:
- Windows 10 and 11
- Windows Server 2016, 2019, and 2022
- macOS Ventura and Sonoma
- Linux:
- RHEL versions 7, 8, and 9
- Oracle Linux version 8
- Amazon Linux version 2
- Ubuntu versions 18.04, 20.04, and 22.04
- AlmaLinux versions 8 and 9
- Rocky Linux versions 8 and 9
- Distribution independent benchmarks
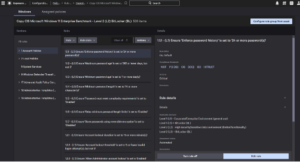
Configuration assessment rule groups are based on standards published by third-party authorities:
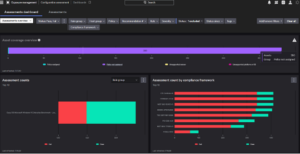
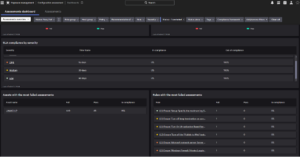
The Assessments dashboard shows high-level info about compliance assessments that were performed in your environment:
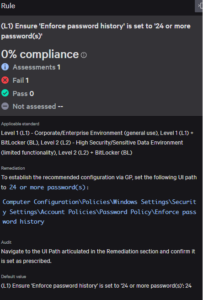
Remediation
Briefly, CrowdStrike introduces a powerful configuration assessment feature within its platform, enabling you to:
✅ Identify misconfigurations
✅ Measure device compliance with pass/fail scores
✅ Support multiple operating systems
✅ Implement remediations to reduce cyber risk
With this automated assessment, you can streamline audit preparation, enhance security posture, and ensure compliance with global benchmarks.
Get started today and take control of your cybersecurity resilience with TEKNOLOGIIA!
Test Your Security Score by Contacting Us: [email protected]
Stay Connected! Subscribe to our LinkedIn Newsletter for expert insights, compliance tips, and the latest security updates.



