Beware of these scams … Hackers don’t need more than your email to do you a lot of damage
How do you submit your information to the hacker?
“When the hacker knows your email address, they have half of your confidential information, and all they need now is the password.” Hackers use many different methods to achieve this, and the most common is a phishing email.
This action is represented in designing an email for a well-known website such as Amazon, eBay, and Paypal, to deceive you and ask you to log in to do something.
Once people log into this fake website, the hacker instantly receives the credentials of the account.
Among other methods, you may receive an email saying that your email has been compromised, so you need to change your password for security reasons.
Once you change your password, the hacker will seize it.
1-What Are Some of the Main Types of Phishing Attacks?
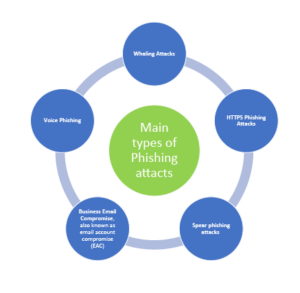
2-What’s the Difference Between Phishing and Spear Phishing?
- Phishing attacks
Phishing attacks are relatively low stakes, and usually, they are easier to recognize than spear phishing attacks. Phishing is an email or electronic communications scam targeted towards random individuals, organizations, or businesses. Although often intended to steal data for malicious purposes, cybercriminals may also intend to install malware on a targeted user’s computer.
Phishing emails are sent to hundreds of recipients simultaneously, and they do not contain personal information.
- Spear phishing attacks
The spear phishers pose as a friend, a boss, a family member, or a social media organization to gain your trust and fool you into giving them your information via email scams. This type of email scam is well-researched and personal, which makes it harder to distinguish between what is real and what is fake.
Spear phishing, in contrast, is highly targeted and targets a single individual. Hackers do this by pretending to know you. It’s personal. A spear-phishing attacker is after something in particular.
3-What happens if your account gets hacked?
- Access to your electronic accounts
Many people tend to use the same password to log in to their online accounts, in which the hacker gains access to many other accounts effortlessly.
But even if you use different passwords, the hacker can click on the “forgot password” field for your accounts so that he can either resubmit the password or request a new password.
- Viewing your personal data
The things that hackers can do are linked together and are chain reactions.
Once a hacker accesses your online accounts, you can imagine how much information he will be able to collect. The hacker will use your email address to access your Facebook account, dig into your friends’ list, and steal some of your photos.
If that wasn’t enough, the hacker will put your email address on the “LinkedIn” site and searched for you; he would know your workplace, your job, your colleagues, and the places you studied before.
This information is enough for the hacker to start stalking you in the real world, not to mention the possibility of obtaining other information from Instagram and Twitter.
- Theft of your financial data
And big problems will begin to arise as soon as the hackers obtain your credit or bank card data, so you must have sent this data by email at some point.
Overall, this leads to making your online banking accounts a prime target for hackers; especially if you use your email address to log into them.
Once your email is compromised, funds are at risk, as it will be easy to reset the bank account and start issuing transactions. Hackers can open bank accounts in your name and obtain loans, as well as spoil your credit card rating.
- Blackmail you
If all of the above are not scary enough, you must know that hackers can use your personal information to harm and destroy your reputation and threaten you, especially if the user finds something that they can use against you because you do not want to trade in public. In this regard, Hackers can spy on you and review most of your emails and find certain private information to blackmail you easily.
- Impersonation of your identity
Impersonation is the worst-case scenario ever since the hacker has obtained all of your private information and personally identifiable information for himself. And since email can contain credit card information, identity theft can come in handy for hackers.
5-So how can you stay safe from intruders and timeless scams?
Malware and ransomware variants change quickly, but phishing and spear-phishing are still the most effective ways to deliver them. Security analysts need a broad security background to interpret what is going on to identify new indicators, search for them across all systems, and apply blocking measures.
Having our experienced Teknologiia team staff is essential to these types of attacks every day and surviving them. Teknologiia manages to offer you a security service solution that enables them to secure your endpoints more effectively while lowering operational costs and demonstrating a faster return on your next-gen EDR investment.
If you’re concerned about spear-phishing and other advanced threats that can impact your organization, we, at Teknologiia, can provide you with a next-gen EDR endpoint protection platform that offers you advanced protection over traditional antivirus.
In conclusion, if there are many connected devices in your environment, you must be prepared to handle a potentially large volume of alerts and spend some time upfront on fine-tuning the solution.
The average cost of recovering from a ransomware attack is 20 times more than putting proper endpoint security and 24×7 SOC in place today.
Don’t hesitate to contact us, and our experts will gladly assist and support you in staying secure.
Ask the experts! Teknologiia Subscribe on LinkedIn


